Centralization is coming. The Gods heard our pleas and ceased to contribute to the growth of the army of the Night King. The Lords of Westeros responded to the call of Jon Snode and arrived at the first military Council to Winterfell. During the discussion of the strategy to fight the army of dead lessors, the doors of the Hall suddenly opened and Brandon Stark appeared in front of the Lords. His anxious eyes were bent fixedly on Jon:
-Jon, I had visions.
-Bran, can this wait until the end of the Council? - John was very concerned about the Lords’ worries, as well as the fact that not all Lords take the impending threat seriously.
-I am afraid, no… Jon, you should know this. I saw the Westeros ruined. I saw the end of this world and the triumph of the Night King. We have very little time left. The Wall is destroyed.
There was a chilling silence in the Hall.
-Ok, Bran. What did you see? Please, speak up.
Attention! All the information that follows is the result of the coordinated hard work of people who care about the future of the Waves Platform. We do not want to cause any harm to the ecosystem. Our goal is to strengthen and improve it.
The essence
Since the beginning of the Game of Nodes several initiative groups have been created. Different tasks were assigned to these groups. One of the groups got the task to demonstrate in practice the possible and most dangerous vector of attack on the Waves Platform. This means the following:
- We did not conduct an attack on the main Waves MAINNET blockchain.
- However, within this group of people we created almost the full copy of MAINNET. We did not just prove that the attack is real, we actually performed it on the copy of MAINNET.
- To perform the attack, the latest 0.13.4 version of the node was used. It is the version that MAINNET is currently using.
- You do not need programming skills in order to attack the blockchain network. The entire attack was conducted without any changes to the code.
- To conduct an attack it is desirable, but it is not actually required, to have access to the configurations of the nodes via which this attack is carried on. Moreover, the nodes can be used blindly, so that their owners do not have a clue.
- A successful attack can bring a huge profit to the attacker (or attackers). It can also lead to a complete dump of the Waves price. If such an attack really happens in the MAINNET, then all your Waves will not cost a dime.
- All this is possible only because the Waves network has reached a critical level of centralization. The fight against centralization is our top priority. Therefore, we do not aim to attack the MAINNET, we do not sell our knowledge and experience, but we urge you not to allow such an attack occur in the future.
Summary
For those who do not have deep technical knowledge but possess the Waves tokens we briefly describe the essence of the attack.
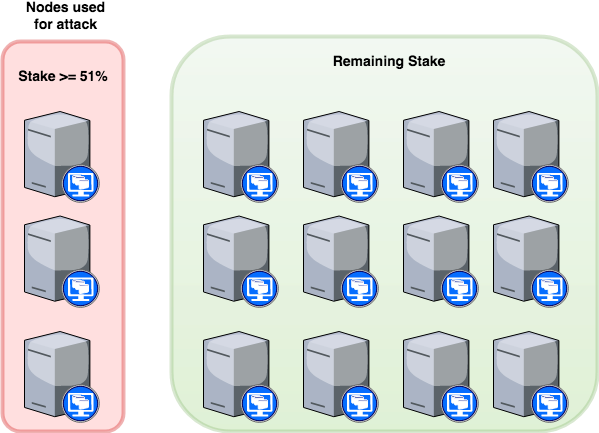
At the moment there are about 90 nodes (servers), that generates blocks. Those nodes represent a single network also known as blockchain. Each of these nodes has a certain generating balance. The size of generating balance determines the right of a particular node to add (to write) the next block to the blockchain. The more the generating balance, the more chances to write the next block. As a result, the nodes with large generating balances add more blocks to the blockchain. Currently, the first 3 nodes (aka top nodes) write in total about 60% of all blocks, which makes these nodes potentially dangerous. The thing is that the temporary disconnection of those nodes from the main network still retains their right to prevail in the main network. If a node is disconnected from the main network for less than 100 minutes (which is roughly equivalent to generating 100 new blocks), then all this time its generating balance is still considered by the network.
During these 100 minutes, the attackers can send tens or hundreds of thousands of Waves to any other exchange or any other external platform, where those Waves can be easily spent. It can be the Binance exchange, for example. Further the attackers can sell all their Waves on different exchanges and platforms. After using the entire markets liquidity, attackers can quickly initiate the withdrawal of BTC, ETH, LTC, etc. on from these platforms to their wallets. All this takes about 30-40 minutes. As soon as the funds are withdrawn, the attacking nodes will be connected back to the main network and all transactions that have been conducted with Waves will be canceled inside the Waves Platform. The attacker will get back their “spent” Waves. At the same time the intruders also remain with their BTC, ETH, LTC, etc. on the wallets, which they managed to get off the platform.
The Waves price will be dumped as well as its reputation. And, perhaps, we will witness the appearance of Waves Classic.
Notes before attack explanation
Blockchain = governance
Before entering into details about a 51% attack, it is important to understand that blockchain protocols are basically a form of governance. A blockchain governs a ledger of data, for example transaction data. Because the blockchain software can govern this for us, we no longer need a third party to do this, such as a government or bank. This is what makes (most) blockchains decentralized. The protocol of the Waves blockchain is based on democracy, meaning that the majority of the participants (miner nodes) on the network will get to decide what version of the blockchain represents the truth.
How a 51% attack works
Let’s put it simple. When a transaction is signed off on by a Waves owner, it is put into the pool of unconfirmed transactions. Miner nodes select transactions from this pool to form a block of transactions. In order to add this block of transactions to the blockchain, they need to have a right to generate new block. The bigger generation balance is on the node, the better probability or its chances that the node generate new block. As soon as a node generate a block and put transactions there (in microblocks), it will broadcast it to the other miner nodes and they will only accept it if all transactions inside that block are valid according to the existing record of transactions on the blockchain. Note that even a corrupted mining node can never create a transaction for someone else because they would need the digital signature of that person in order to do that (their private key). Sending Waves from someone else’s account is therefore simply impossible without access to the corresponding private key.
Waves Blockchain 51% Attack
Disclaimer: For the attack we have created our own private blockchain network based on Waves Platform (version 0.13.4) and reproduce leasing pools proportions based on Waves MAINNET.
Some general comments:
- No code changes to waves platform codebase have been added.
- Only LEASING Waves have been used during the attack for generating balances distribution.
- Attacker doesn’t risk his own money, as used leasing money granted to his leasing pool. This can be achieved because of LPOS algorithm being used by Waves.
- Attack can be achieved by the agreement of Leasing Nodes owners, one or more, the only need is to have more or equal to 51% of generating balance power.
- Attack can be achieved even without the agreement of Leasing Nodes owners, because it is done by networking tools only, so it can be achieved by traffic operators or some “Man-in-the-middle” firewall technics.
Preconditions:
- Private blockchain based Waves Platform 0.13.4.
- Waves wallet connected to main blockchain.
- Waves wallet connected to a node used for attack.
- 15 mining nodes with total generation balance of 42 000 000 Waves.
- 3 top nodes have 60% mining power or 25 200 000 Waves.
- 3 top nodes can be controlled by one authority.
- Wallet A and Wallet B controlled by the Attacker.
- Wallet C - external address (exchange, where Waves have been listed or any other trading platform with Waves as a payment option) to transfer funds out of the current blockchain.
Attack scenario
Step 1: Separate chains
3 top nodes were excluded from main blockchain at some Height, e.g. 3045, but continue to communicate with each other. Thus, blockchain splits into two separate chains: malicious and original one.
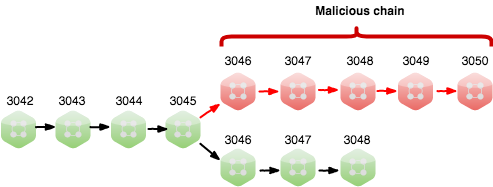
Now we have two versions of the same blockchain. Both chains mine new blocks, but Malicious chain doesn’t see blocks of Original one and vice versa.
Step 2: Create double spend transaction
Attacker creates two transactions:
- In offline chain: TX1 - transfer all Waves from Wallet A to Wallet B.
- In online chain: TX2 - transfer all Waves from Wallet A to Wallet C.
So, we have TX1 at 3046 Height in Malicious Chain. And TX2 at 3047 Height in Original Chain.
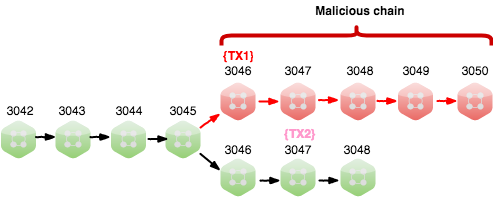
At this time we have spent the same amount from one wallet - Wallet A, but in different chains.
The blockchain is programmed to follow a model of democratic governance, aka the majority. The blockchain does this by always following the longest chain, after all, the majority adds blocks to their version of the blockchain faster than the rest of the network. This is how the blockchain determines which version of its chain is the truth, and in turn what all balances of wallets are based on.
Step 3: Merge chains
The corrupted authority will now try to add blocks to his isolated blockchain faster than the other mining nodes add blocks to their blockchain (the truthful one). As soon as the corrupted authority achieves a longer blockchain, he connected to the main chain and broadcasts this version of the blockchain to the rest of the network. The rest of the network will now detect that this (corrupted) version of the blockchain is actually longer than the one they were working on, and they are forced to switch to this chain.
The corrupted blockchain is now considered the truthful blockchain, and all transactions that are not included on this chain will try to apply to it in new blocks. But the transaction from Wallet A to Wallet C cannot be applied, as money out of blockchain already. As all Waves already sent to Wallet B, and the attacker controls Wallet A and Wallet B, he is now once again in control of those Waves. He is able to spend them again. Important, that the total amount of transferred Waves on Wallet C must be out of the current blockchain before merging, e.g. have been sent to some exchange.
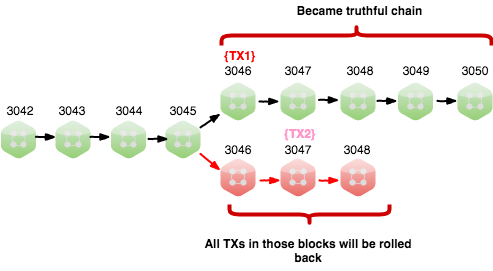
All transactions from shorter blockchain that cannot be recovered, will be rolled back. This is a double-spend attack, assuming that amounts are transferred out of the blockchain during attack. It is commonly referred to as a 51% attack because the malicious miner will require more leasing power than the rest of the network combined (thus 51% of the leasing power) in order to add blocks to his version of the blockchain faster, eventually allowing him to build a longer chain.
Stay tuned, next chapter of the Game of Nodes is on the way.
